Facts:
- Web extensions save lives (I use the term ‘facts’ very loosely).
- Recently a web extension installed by a school user was hijacked to redirect YouTube advertising to pornographic content.
- A hijacked extension applied to one device is capable of impacting multiple users on a network.
- Removing the extension removes the threat.
If you know anything about browser applications and web extensions, you’ll know they’re incredibly handy (they don’t call them productivity tools for nothing). These tools are designed to ‘extend’ the functionality of your browser and I for one use them all the time. From URL shorteners, screencasting tools to content curation services, I simply wouldn’t be without my extensions. But like all good things today, these extensions need to carry a warning. The sad reality is that those ‘bad people’ I spoke of in an earlier post (see here) can use the tools found in browser web stores to hijack your computer by installing malware. Yes, there really are nutters out there looking to disrupt your online experience.
For clarity:
Malware = malicious software that is used to disrupt, corrupt or takeover a computer or network.
Case in point:
Earlier this year, N4L responded to a case where a school was infected with malware contracted via the ‘Web Paint’ extension from the Google Chrome Web Store.* In this instance, the extension was ‘hijacked’ by a hacker who inserted malicious code into the extension’s script. The script was then used to redirect standard YouTube advertising to pornographic content. The result was that when the user opened videos on YouTube, all standard advertising was replaced with inappropriate content. Not what you want – especially if you’re a teacher using YouTube to demonstrate an important educational concept.
Web extension hijacking happens. What is particularly troubling for schools is the impact it can have on a school network. If one hijacked extension is installed on one user’s account, it is possible for the corrupt script to affect all users on the network (in a kind of three musketeers scenario) – whether other users have installed the extension or not.
Obviously, this is incredibly problematic, and it should be noted that replacing standard advertising with pornography is just one example highlighting the impact of extension hijacking. Hijacking can result in the distribution of viruses, ransomware and server attacks. In other words, hijacking = bad (#CaptObvious).
Which is exactly why it is something schools need to be aware of.
What can schools do?
The good news is that removing the corrupt extension removes the associated threat. Admittedly, this is a reactive response but even so, this should bring schools some comfort.
It’s also the only clear ‘solution’ we can offer.
While there are mitigating steps that a school can implement, the difficulty is that there isn’t a silver bullet. The very thing that makes web extensions and applications awesome is also the reason it’s a difficult problem to solve; an abundance of tools. These tools are created by people like you or me (well, not necessarily you or me but you get the idea), which means the resources behind these tools and their subsequent robustness are varied. Put simply, established companies have robust safety checks in place to scrutinise their resources and protect the security of their products.
Here are some things schools can do to limit the risks of extension hijacking:
- Don’t Panic: there is no need to implement a blanket ban of apps and extensions – this would do more harm than good. Extension hijacking is real, but it’s also not rife – don’t batten down the hatches, just be aware of the problem.
- Educate: Encourage users to be selective in their use of extensions.
-
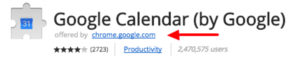
- Apply scrutiny before adding the tool to your browser – identify who has produced it and whether they are a trustworthy user/company. If they are an individual with a private name/email address, check with your administrator before installing the tool.
-
Image: Verify the tools creator
-
- Read user reviews and support information – and don’t just accept the good reviews. Users generally provide honest feedback, but it’s important to look beyond the glowing reviews, read the negative ones too (you’ll learn much more this way).
-
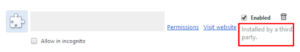
- Periodically review your extensions and remove any installed by third parties.
Image: Red flag – extensions ‘Installed by a third party’
Gif: How to remove chrome extensions
- Remove & Report: If you do notice any strange activity on your device, remove any extensions that may have been installed recently and report any attacks via the webstore’s ‘Report Abuse’ service.
- Scan IT: Ensure your antivirus is up-to-date and running on a regular basis. Anti-virus software produce regular updates that are designed to protect your network by intercepting threats. If you’re not scanning it, you’re not protecting your machine or your network.
Ultimately, deleting a suspicious extension removes the associated threat that may have introduced malicious activity on your network. If in doubt, remove the extension and if symptoms persist, contact our help desk on 0800 LEARNING, or your school’s N4L Client Manager (between you and me, they really like solving problems).
_____
Not familiar with web extensions?
Learn more about Chrome extensions here and Mozilla here or run a simple search on your browser of choice.
_____
* The hijacked ‘Web Paint’ application was fixed on the 6th March 2017 – review the extensions notes here for more information.


Hi, I would like to subscribe for this website to obtain newest updates,
so where can i do it please help.
Hi Isabel, we don’t currently have a subscribe function but it’s coming soon.